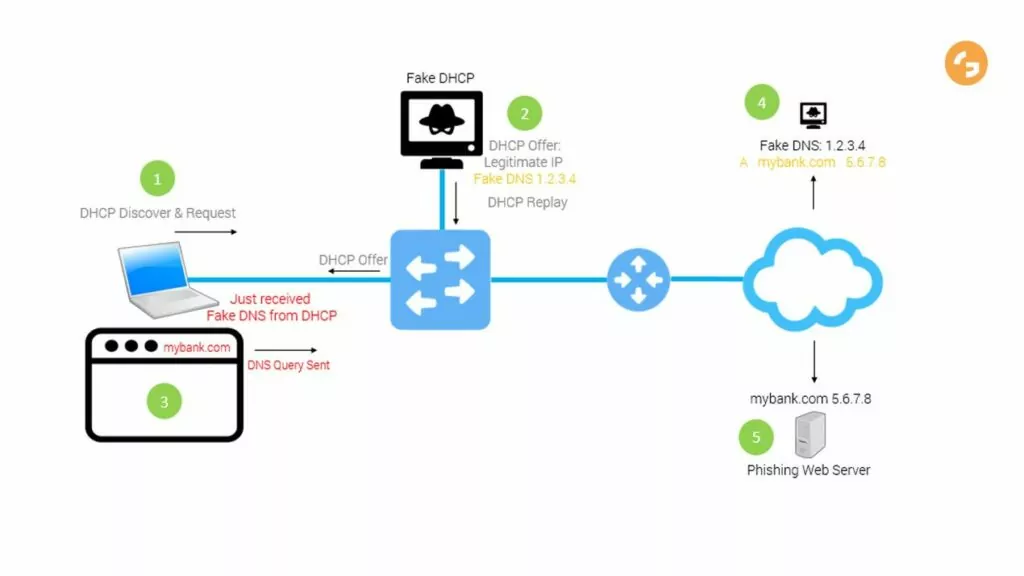
The broadcast storm attack: The bold line with arrow represents normal... | Download Scientific Diagram
![PDF] Denial of Service Due to Direct and Indirect ARP Storm Attacks in LAN Environment | Semantic Scholar PDF] Denial of Service Due to Direct and Indirect ARP Storm Attacks in LAN Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2571b39da7e105ecef895108b592f51939b687de/3-Figure1-1.png)
PDF] Denial of Service Due to Direct and Indirect ARP Storm Attacks in LAN Environment | Semantic Scholar
![PDF] Detection and mitigation of ARP storm attacks using software defined networks | Semantic Scholar PDF] Detection and mitigation of ARP storm attacks using software defined networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e87c50928b1161eb125b7baea1975de0e37f1f11/2-Figure2-1.png)
PDF] Detection and mitigation of ARP storm attacks using software defined networks | Semantic Scholar
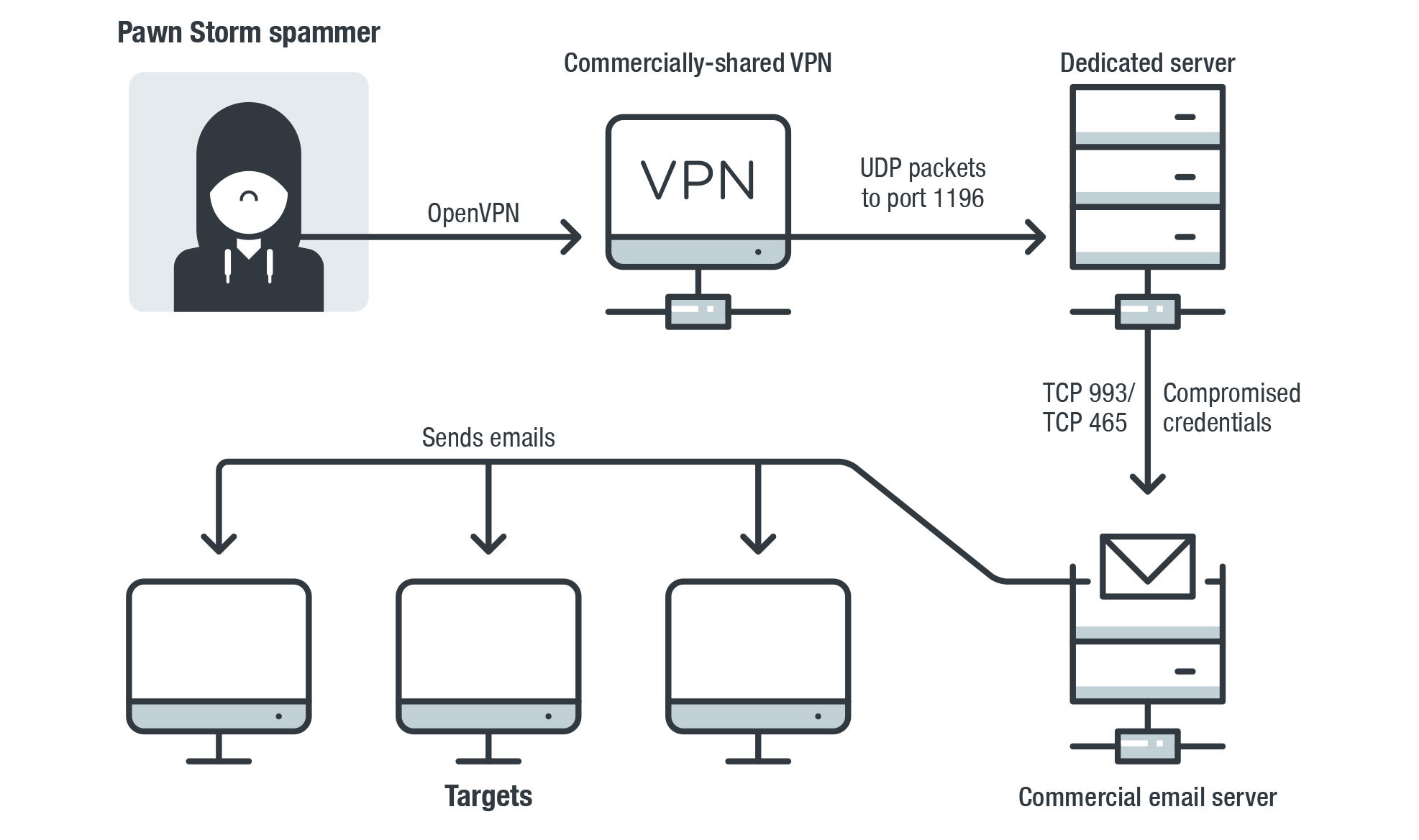


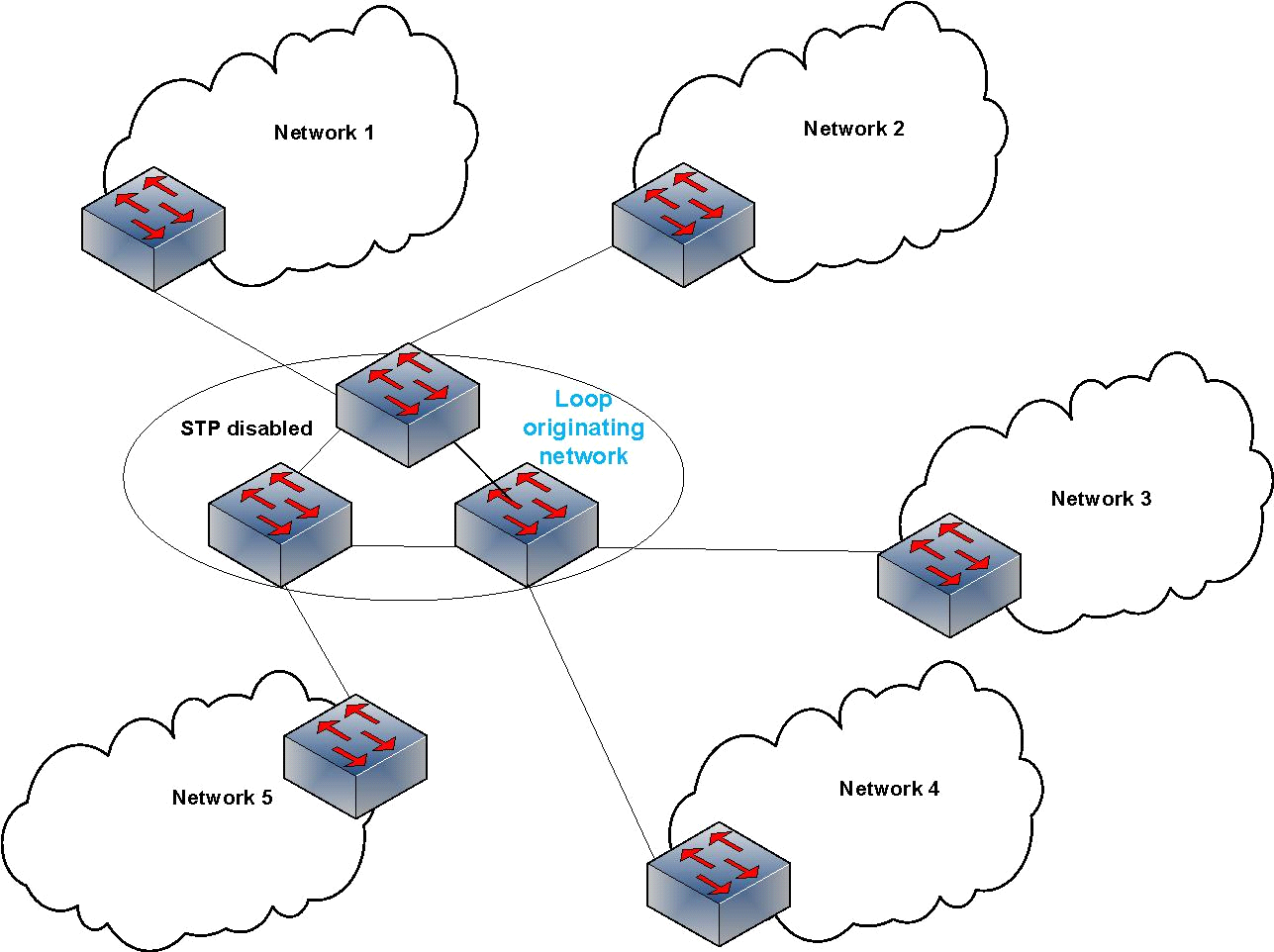


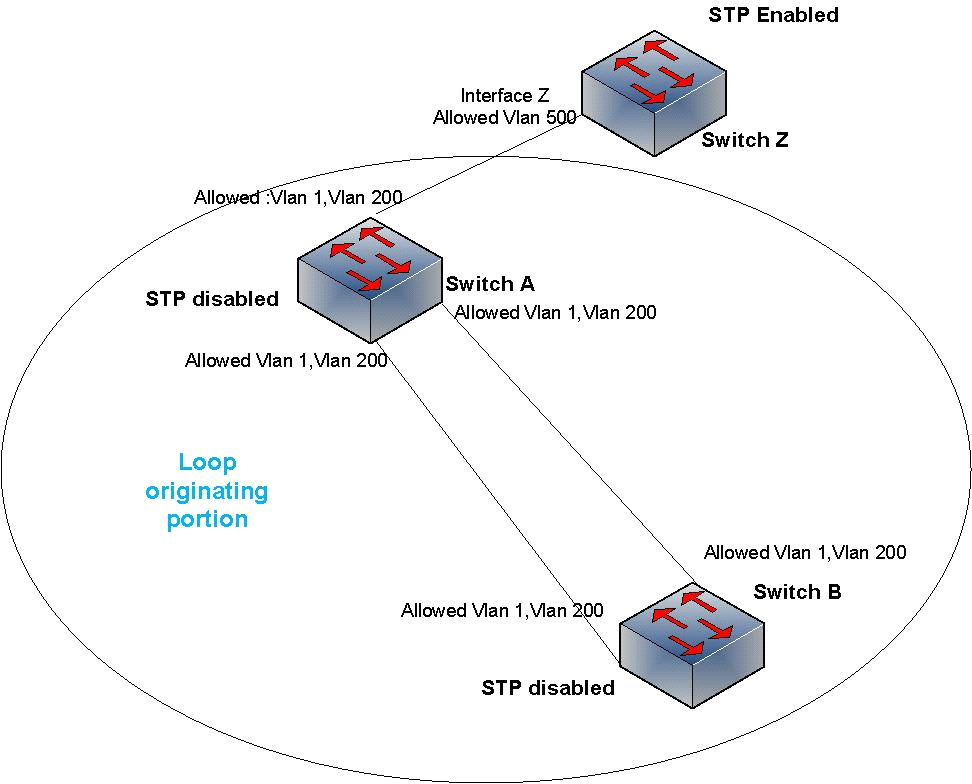




![PDF] Mitigating Broadcast Storm on Metro Ethernet Network Using PVST | Semantic Scholar PDF] Mitigating Broadcast Storm on Metro Ethernet Network Using PVST | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6a807083bc9123f3b9e863f20832ee1f9a2ed18f/2-Figure1-1.png)